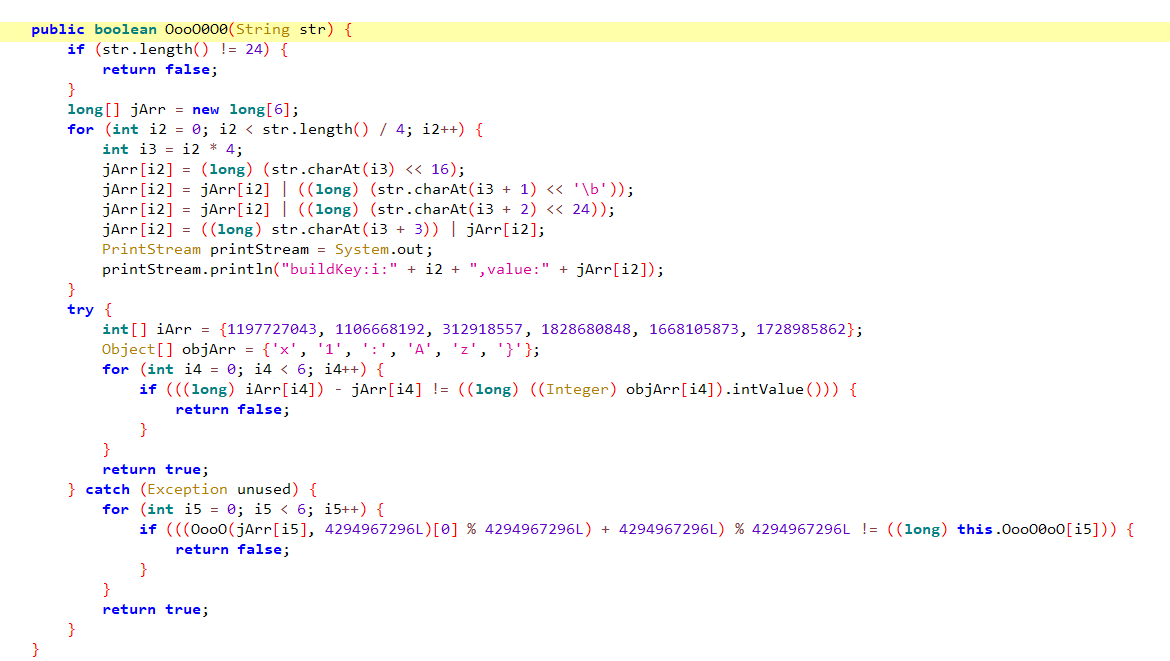
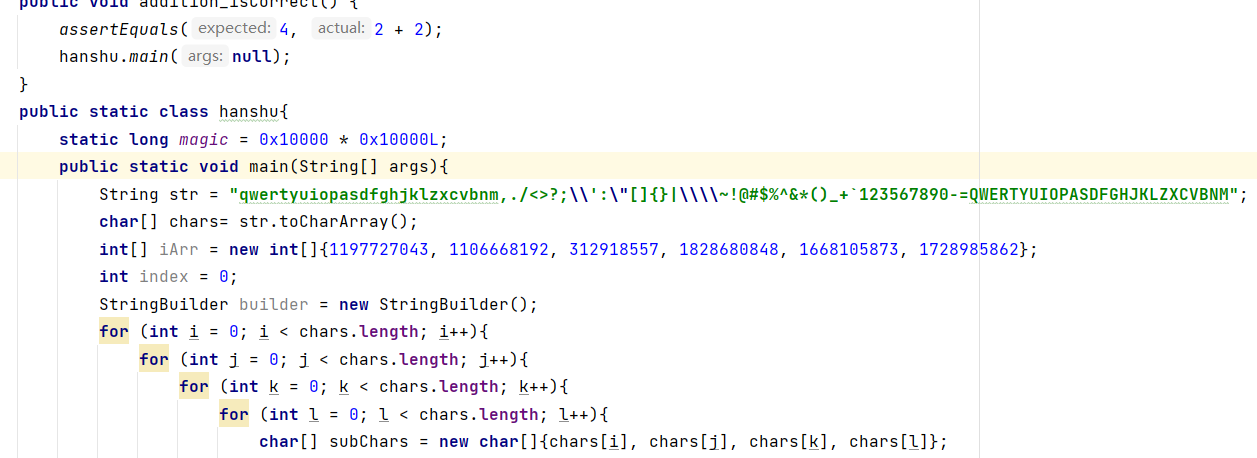
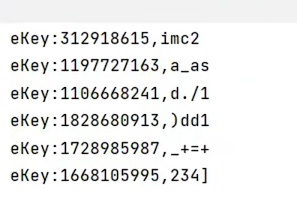
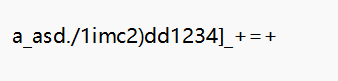
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| 2022-10-19T03:12:07.961675Z 12 Query INSERT INTO `member` VALUES (973, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13532680973', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo973', 1, NULL, 0, '2022-10-18 13:4:24', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1973', '2022-10-18 13:4:24', 1, NULL, 0, '13532680973', NULL, NULL, '中国', 0, 3, 0, 0, NULL)
2022-10-19T03:12:07.968287Z 12 Query INSERT INTO `member` VALUES (974, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13176680974', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo974', 1, NULL, 0, '2022-10-18 14:14:4', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1974', '2022-10-18 14:14:4', 1, NULL, 0, '13176680974', NULL, NULL, '中国', 0, 5, 0, 0, NULL)
2022-10-19T03:12:07.974085Z 12 Query INSERT INTO `member` VALUES (975, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13530690975', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo975', 1, NULL, 0, '2022-10-18 15:23:44', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1975', '2022-10-18 15:23:44', 1, NULL, 0, '13530690975', NULL, NULL, '中国', 0, 3, 0, 0, NULL)
2022-10-19T03:12:07.979831Z 12 Query INSERT INTO `member` VALUES (976, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13942370976', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo976', 1, NULL, 0, '2022-10-18 16:33:24', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1976', '2022-10-18 16:33:24', 1, NULL, 0, '13942370976', NULL, NULL, '中国', 0, 1, 0, 0, NULL)
2022-10-19T03:12:07.985614Z 12 Query INSERT INTO `member` VALUES (977, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13486370977', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo977', 1, NULL, 0, '2022-10-18 13:4:43', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1977', '2022-10-18 13:4:43', 1, NULL, 0, '13486370977', NULL, NULL, '中国', 0, 5, 0, 0, NULL)
2022-10-19T03:12:07.991726Z 12 Query INSERT INTO `member` VALUES (978, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13840370978', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo978', 1, NULL, 0, '2022-10-18 14:14:23', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1978', '2022-10-18 14:14:23', 1, NULL, 0, '13840370978', NULL, NULL, '中国', 0, 3, 0, 0, NULL)
2022-10-19T03:12:07.996485Z 12 Query INSERT INTO `member` VALUES (979, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13384370979', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo979', 1, NULL, 0, '2022-10-18 15:24:3', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1979', '2022-10-18 15:24:3', 1, NULL, 0, '13384370979', NULL, NULL, '中国', 0, 1, 0, 0, NULL)
2022-10-19T03:12:08.002778Z 12 Query INSERT INTO `member` VALUES (980, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13738370980', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo980', 1, NULL, 0, '2022-10-18 16:33:43', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1980', '2022-10-18 16:33:43', 1, NULL, 0, '13738370980', NULL, NULL, '中国', 0, 5, 0, 0, NULL)
2022-10-19T03:12:08.008331Z 12 Query INSERT INTO `member` VALUES (981, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13282380981', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo981', 1, NULL, 0, '2022-10-18 13:15:36', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1981', '2022-10-18 13:15:36', 1, NULL, 0, '13282380981', NULL, NULL, '中国', 0, 3, 0, 0, NULL)
2022-10-19T03:12:08.013494Z 12 Query INSERT INTO `member` VALUES (982, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13736380982', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo982', 1, NULL, 0, '2022-10-18 14:25:16', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1982', '2022-10-18 14:25:16', 1, NULL, 0, '13736380982', NULL, NULL, '中国', 0, 5, 0, 0, NULL)
2022-10-19T03:12:08.019163Z 12 Query INSERT INTO `member` VALUES (983, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13248060983', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo983', 1, NULL, 0, '2022-10-18 15:34:56', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1983', '2022-10-18 15:34:56', 1, NULL, 0, '13248060983', NULL, NULL, '中国', 0, 3, 0, 0, NULL)
2022-10-19T03:12:08.023970Z 12 Query INSERT INTO `member` VALUES (984, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13692060984', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo984', 1, NULL, 0, '2022-10-18 16:44:36', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1984', '2022-10-18 16:44:36', 1, NULL, 0, '13692060984', NULL, NULL, '中国', 0, 1, 0, 0, NULL)
2022-10-19T03:12:08.030725Z 12 Query INSERT INTO `member` VALUES (985, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13146060985', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo985', 1, NULL, 0, '2022-10-18 13:15:55', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1985', '2022-10-18 13:15:55', 1, NULL, 0, '13146060985', NULL, NULL, '中国', 0, 5, 0, 0, NULL)
2022-10-19T03:12:08.035551Z 12 Query INSERT INTO `member` VALUES (986, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13590070986', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo986', 1, NULL, 0, '2022-10-18 14:25:34', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1986', '2022-10-18 14:25:34', 1, NULL, 0, '13590070986', NULL, NULL, '中国', 0, 3, 0, 0, NULL)
2022-10-19T03:12:08.040445Z 12 Query INSERT INTO `member` VALUES (987, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13844070987', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo987', 1, NULL, 0, '2022-10-18 15:35:14', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1987', '2022-10-18 15:35:14', 1, NULL, 0, '13844070987', NULL, NULL, '中国', 0, 6, 0, 0, NULL)
2022-10-19T03:12:08.048228Z 12 Query INSERT INTO `member` VALUES (988, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13388070988', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo988', 1, NULL, 0, '2022-10-18 16:44:54', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1988', '2022-10-18 16:44:54', 1, NULL, 0, '13388070988', NULL, NULL, '中国', 0, 4, 0, 0, NULL)
2022-10-19T03:12:08.053610Z 12 Query INSERT INTO `member` VALUES (989, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13742070989', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo989', 1, NULL, 0, '2022-10-18 13:26:47', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1989', '2022-10-18 13:26:47', 1, NULL, 0, '13742070989', NULL, NULL, '中国', 0, 2, 0, 0, NULL)
2022-10-19T03:12:08.058670Z 12 Query INSERT INTO `member` VALUES (990, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13353750990', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo990', 1, NULL, 0, '2022-10-18 14:36:27', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1990', '2022-10-18 14:36:27', 1, NULL, 0, '13353750990', NULL, NULL, '中国', 0, 4, 0, 0, NULL)
2022-10-19T03:12:08.066046Z 12 Query INSERT INTO `member` VALUES (991, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13797750991', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo991', 1, NULL, 0, '2022-10-18 15:46:7', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1991', '2022-10-18 15:46:7', 1, NULL, 0, '13797750991', NULL, NULL, '中国', 0, 2, 0, 0, NULL)
2022-10-19T03:12:08.070986Z 12 Query INSERT INTO `member` VALUES (992, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13251760992', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo992', 1, NULL, 0, '2022-10-18 16:55:47', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1992', '2022-10-18 16:55:47', 1, NULL, 0, '13251760992', NULL, NULL, '中国', 0, 6, 0, 0, NULL)
2022-10-19T03:12:08.076234Z 12 Query INSERT INTO `member` VALUES (993, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13695760993', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo993', 1, NULL, 0, '2022-10-18 13:27:6', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1993', '2022-10-18 13:27:6', 1, NULL, 0, '13695760993', NULL, NULL, '中国', 0, 4, 0, 0, NULL)
2022-10-19T03:12:08.081554Z 12 Query INSERT INTO `member` VALUES (994, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13149760994', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo994', 1, NULL, 0, '2022-10-18 14:36:46', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1994', '2022-10-18 14:36:46', 1, NULL, 0, '13149760994', NULL, NULL, '中国', 0, 2, 0, 0, NULL)
2022-10-19T03:12:08.086191Z 12 Query INSERT INTO `member` VALUES (995, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13593760995', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo995', 1, NULL, 0, '2022-10-18 15:46:26', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1995', '2022-10-18 15:46:26', 1, NULL, 0, '13593760995', NULL, NULL, '中国', 0, 6, 0, 0, NULL)
2022-10-19T03:12:08.091434Z 12 Query INSERT INTO `member` VALUES (996, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13947760996', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo996', 1, NULL, 0, '2022-10-18 16:56:6', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1996', '2022-10-18 16:56:6', 1, NULL, 0, '13947760996', NULL, NULL, '中国', 0, 4, 0, 0, NULL)
2022-10-19T03:12:08.097094Z 12 Query INSERT INTO `member` VALUES (997, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13459440997', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo997', 1, NULL, 0, '2022-10-18 13:37:59', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1997', '2022-10-18 13:37:59', 1, NULL, 0, '13459440997', NULL, NULL, '中国', 0, 6, 0, 0, NULL)
2022-10-19T03:12:08.101734Z 12 Query INSERT INTO `member` VALUES (998, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13913450998', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo998', 1, NULL, 0, '2022-10-18 14:47:39', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1998', '2022-10-18 14:47:39', 1, NULL, 0, '13913450998', NULL, NULL, '中国', 0, 4, 0, 0, NULL)
2022-10-19T03:12:08.108159Z 12 Query INSERT INTO `member` VALUES (999, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13457450999', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo999', 1, NULL, 0, '2022-10-18 15:57:19', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c1999', '2022-10-18 15:57:19', 1, NULL, 0, '13457450999', NULL, NULL, '中国', 0, 2, 0, 0, NULL)
2022-10-19T03:12:08.113211Z 12 Query INSERT INTO `member` VALUES (1000, NULL, NULL, 0, 0, NULL, NULL, NULL, NULL, NULL, NULL, NULL, 0, 0, NULL, 0, NULL, NULL, 0, NULL, NULL, 0, NULL, NULL, NULL, '中国', NULL, NULL, 0, 0, NULL, 0, '13811451000', 'ee455f8f8e5d321861ed7ef5bde6dbc5', 'U000001Lo1000', 1, NULL, 0, '2022-10-18 17:6:59', '353233323433333238363833323439363634', 0, b'1', 0, 0, 'c3d54ed7-b20f-430b-8f9a-b517c11000', '2022-10-18 17:6:59', 1, NULL, 0, '13811451000', NULL, NULL, '中国', 0, 6, 0, 0, NULL)
|